Zekt is the event bus that connects GitHub workflows across organizations — without sharing access.
It removes the friction of secure event and messaging exchange between organizations by letting teams request & approve interaction. Zekt handles the brokering and orchestrates events & messages across GitHub organizations — transparently, securely, and without managing credentials.
Common Challenges Today
The problems that Zekt addresses
How Zekt Solves This
Three core capabilities
Standardized Event Workflows
Zekt exposes your GitHub organization's workflows as managed, repeatable event & message streams. No custom integrations. No bespoke code. Just workflows events & optional rich JSON meta-data that consumers can subscribe to & act upon.
Federated Identity & Control
Providers stay in complete control. Every consumer request requires explicit approval by the provider. Zekt uses GitHub OIDC - no shared secrets, no service principals lying around. You are consenting to the Github apps - you are in control & permissions needed are transparent to you upon onboarding
Transparent Data Governance
Only event (optionally messages) metadata reaches consumers - never sensitive repo details or credentials. Audit trails are automatic. Compliance teams see exactly what happened, when, and who approved it. Zekt revolves around events & messaging - what ran, by whom & who does it concern?
When Things Go Wrong — Time Travel
Your most critical capability: replay any event, exactly as it happened
What happens when an event fails? When a consumer changes their workflow? When you need to prove what was delivered 60 days ago?
Zekt's Time Travel capability lets you replay any historical event with structural fidelity — the replayed event is identical to the original. Consumer workflows process it the same way. No manual re-construction. No guessing. No payload drift.
Example — Incident Recovery with Time Travel
Scenario:
A consumer's workflow had a bug — 47 events were processed incorrectly overnight. The consumer fixes their workflow. Now what?
Flow:
Why this matters: No competitor guarantees structural fidelity on replay. Zapier re-runs entire zaps. Pipedream replays individual steps. GitHub retries for 3 days then gives up. Zekt replays the exact event — your consumer workflows won't know the difference.
The Value Zekt Creates
For your business and your teams
Faster Collaboration
Providers define workflows once. Consumers subscribe instantly. No back-and-forth emails.
Governance by Default
Providers control exactly who can do what. Audit trails are automatic and immutable.
Security Built-In
No shared credentials. No token sprawl. Identity-driven permissions using GitHub and Azure.
Operational Clarity
Event metadata only. Consumers never touch provider secrets or sensitive infrastructure.
Scalable by Design
Add consumers and providers without building custom integrations. Zekt scales transparently.
Compliance Ready
Audit logs, approval workflows, and fine-grained access control built in from day one.
Pure Eventing - The Zekt Way
Sometimes information sharing is not needed, like in highly regulated industries - it's more about who did what when
Optional Messaging - The Zekt way
Sometimes messaging is desired to provide actionable next steps. Use zekt-action (GitHub action) to distribute messages if needed
How It Works in Practice
Read up on Zekt terminology and personas
Example 1 — Cross-Team Deployment Events Without Sharing Access
Personas:
- Provider: A team running a CI/CD pipeline
- Consumer: A partner team needing to react to deployments
Scenario:
Your CI/CD workflow finishes. A partner team must run checks — but shouldn't see your repo or secrets, and you don't want to give them access.
Flow:
Business Value: Cross-team automation without permission friction • Zero-trust: workflows react without needing repo or secret access • Faster operations and reduced manual coordination.
Example 2 — Process-to-Audit Automation Loop
Personas:
Two customers, each acting as both providers and consumers
Example use-case: internal process completion → external audit verification
Scenario:
A company runs an internal process workflow. When it completes, an external audit team must verify the result. When the audit finishes, the result must be routed back to the original team.
Flow:
Business Value: Fully automated process + audit loops across organizational boundaries • No access sharing between internal teams and auditors • Traceable, standardized event routing • Eliminates manual hand-offs, emails, and waiting times.
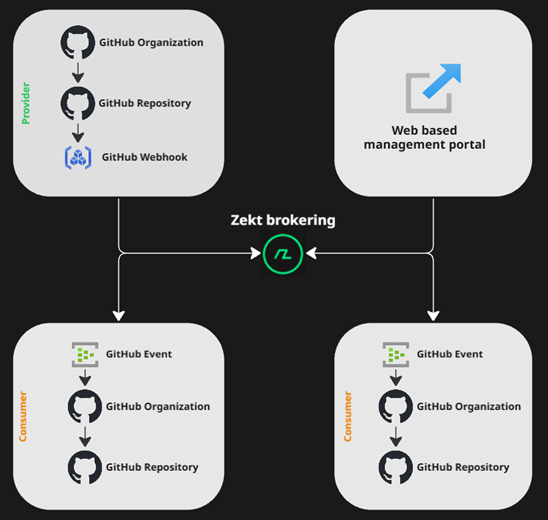
Architecture Overview
How Zekt fits between providers and consumers
Ready to simplify event orchestration?
Join teams that are replacing custom integrations with Zekt's secure, event-driven workflows.